Table of contents
The Internet of Things is one of the next great leaps for business. While many industries already embrace IoT systems, others are still in the early stages of their IoT possibilities.
It’s also a trend that is catching on: in 2022, enterprise spending in IoT development grew by 21.5%. Even amidst turbulent times, big organizations are investing in IoT, while smaller companies are equally gaining. And if surveys are anything to go by, 87% of such projects are meeting business expectations, or better.
As the Internet of Things (IoT) continues to expand, with estimates of billions of devices interconnected globally, the complexity of managing and securing these systems grows exponentially. It’s not just about the sheer volume; it’s the variety of devices and the critical nature of some IoT applications that make addressing these challenges essential for any business looking to capitalize on this technology’s potential.
What is the Internet of Things?
The Internet of Things refers to devices that can connect and exchange data with other devices across the internet and other networks. IoT devices often have sensors, capturing real-world data, or otherwise record, send and process digital data via their software.

IoT devices include a diverse range of smart, connected products like home appliances with remote controls, health-monitoring wearables, sensor-equipped vehicles, and comprehensive systems that help manage everything from urban traffic flow to logistics operations. These are just a few examples of devices in the ever-growing IoT ecosystem.
Of course, the smartphone is also becoming a major player in the IoT world. It processes data, connects to the cloud and can communicate with a multitude of devices. It often acts as a hub for smaller smart devices and wider IoT technology, opening up new potential for businesses.
Companies have become increasingly interested in the Internet of Things due to both the availability of IoT-enabled devices and their general, wide-ranging use cases. Globally, there are approximately 15.14 billion IoT devices, and this number is predicted to grow to 29.4 billion by 2030.[1]

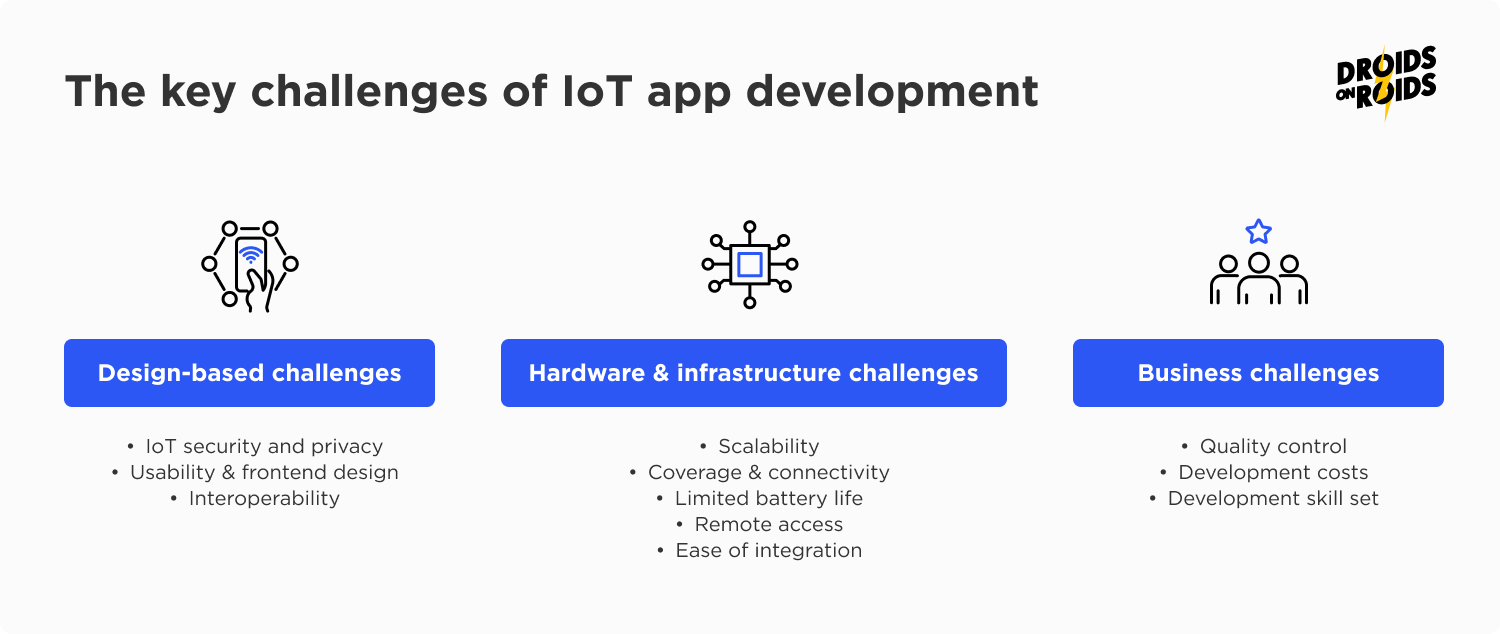
The challenges of IoT app development
Implementing new IoT technologies and business plans does not come without its share of technical challenges. With so many IoT devices out there, businesses face a number of IoT challenges. More than simple device management, companies need to develop cost-efficient ways of managing multiple devices, often from different manufacturers, and the various security challenges, power consumption issues and underlying tech issues that come from adopting such a vast network.
Do it right, and businesses gain a tremendous value for their users, through greater insights and expanded services, and for their own businesses, through advanced analytics capabilities, cost savings and other business applications. Do it wrong, and the costs quickly grow faster than the additional revenue.
For convenience, we have broken down the biggest Internet of Things risks into three main categories, namely:
- Design-based challenges that should be considered at the start when mapping out any IoT application or potential solutions. This covers security issues, app usability and the interoperability of multiple devices.
- Hardware and Infrastructure challenges, covering the physical limitations of sensors and smaller IoT technology, as well as creating a coherent operating environment and architecture for connecting devices of all varieties together.
- Business challenges related to organization issues you might face, from finding desired skill sets to ensuring a high quality service across newly implemented IoT systems and connected devices.
So with all that out of the way, let’s begin!
Design-based challenges
Every device has its own design challenges. With the increasing variety of IoT devices, the number of design considerations also grows. This includes addressing diverse frontends and physical attributes, such as screens and interfaces, as well as ensuring that the underlying software is versatile enough to accommodate all functionalities.
Common IoT risks of this type include usability, interoperability and security. Here, we will answer common concerns such as:
- How will each of our connected devices be used and how will this impact the design?
- How will we ensure each device communicates with each other?
- How will we maintain high security standards across all of our infrastructure?
IoT security and privacy
Security is a top priority in any application but, with the Internet of Things, you also need to consider the additional threats presented across a network of interconnected devices. Often, these devices have varying security levels and, as everyone knows, your security system is only as strong as its weakest point.
And let’s not forget about the sheer volume of data being exchanged. This constant communication only increases the attack surface.
There are many different forms of security that need to be considered here:
- Device security: How is each device secure? What authentication methods are in place to ensure user identities and avoid giving unwarranted access to the wrong people?
- Network security: How is the wider IoT infrastructure secure? If someone gains access, how much of an impact could they cause?
- Data security: How will you ensure privacy? How is data collected, where is it stored and where might it be intercepted?
These are the kind of vital questions that need to always be asked before, during and after IoT development. Whether it’s inadequate encryption, weak authentication mechanisms or insufficient data protection measures, a weak link here can expose sensitive information. It only takes one undefended point of entry to tempt cyberattacks.
- You may also like: 8 Key IoT Security Challenges and Proven Solutions from the Field
Solution
We can still secure the vast Internet of Things by implementing proven methods and practices. We can divide these into a few smaller areas. For example, when dealing with the transmission and storing of data, we should implement:
- End-to-end encryption. Implementing strong encryption protocols aids in protecting data both during transit and at rest. Technologies such as SSL/TLS ensure data remains confidential and secure during transmission.
- Regular firmware updates. Keeping firmware up to date with security patches and fixes will ensure vulnerabilities are addressed as quickly as possible, reducing their risk of exploitation.
- Data minimization. Not every piece of information needs to be sent everywhere. By only storing essential data, we can limit the potential exposure of sensitive information, as well as greatly diminish the impact of any possible data breach.
When it comes to user-based security, there are a number of practices we can implement to help users:
- Multi-Factor Authentication (MFA). By enforcing MFA when users use your IoT devices or applications, we can ensure an additional layer of security and verification. More forms of verification help ensure only known and permitted users gain access.
- User education. It’s also important to educate users, whether it’s the app-using customer or other stakeholders, about best security practices, emphasizing the importance of strong passwords and safe IoT device usage. Some of this can be prompted via design by, for example, notifying the user to change the default password on their IoT app and connected devices.
And from a wider perspective, we can also consider:
- Network segmentation. By segregating IoT devices into separate networks, the attack surface can be minimized. Such an approach isolates compromised devices from critical systems, containing potential threats and limiting the exposure that any one exploitable avenue could cause, limiting the gains for cybercriminals.
- IoT security audits. By routinely auditing your IoT infrastructure, you can uncover and address vulnerabilities early on. This proactive scrutiny ensures that protective measures are continually updated to thwart new and evolving threats effectively.
It’s beneficial to conduct them regularly – they help identify potential vulnerabilities. With this information, you can implement proactive measures to address emerging threats more effectively.
All of these key practices can help mitigate security and privacy issues in IoT app development, safeguarding both data and devices in an interconnected environment.
Usability & frontend design
In the diverse landscape of IoT, usability hinges on creating tailored experiences for each type of device. For instance, smartwatches demand specialized applications designed for their compact screens, distinct from what you would use on a mobile phone or computer screen.
Solution
The key is to design with the user in mind, crafting interfaces that cater to the unique strengths and limitations of each device – simplifying for a smartwatch, while offering more complexity on a mobile device or a full computer display.
Cross-platform technologies like Flutter streamline this process, enabling developers to write a single codebase that works across iOS, Android, web or even Android WearOS platform.
This approach not only ensures a cohesive user experience across different devices but also offers a cost-effective solution to app development, avoiding the need to recreate graphical elements and data structures for each platform.

- You may also like: What is Flutter App Development and How Can It Benefit Your Business?
Interoperability
Imagine receiving a data file that can’t be opened or read. That’s a distinct challenge in the IoT sphere. When devices are abundant, businesses have the challenge of making sure that devices “talk” to each other effectively.
This is due to a distinct lack of standardization that prevents simple “plug and play” infrastructure out of the box. Even after that, someone has to ensure the data is formatted correctly so that it’s recorded and read consistently across the system.
On top of this, there’s also the issue of vendors or lack thereof. What happens when certain devices undergo major updates? What happens to open-source projects? What happens if you also have legacy systems in the loop?
Solution
Different sensors and devices capture their own data differently, so your infrastructure needs to create a consistent approach that will scale better. Common methods include an API that connects with a single source of truth.
By using API as a common integration layer, it’s possible to connect all devices to this layer. Here, the data can be converted to a common format and stored in the cloud. And when devices need data? Simply pull it from this centralized resource.
Through this approach, the only task lies in connecting new devices or sensors into the system or looking at independent updates as necessary. And that’s a whole lot better and more cost-effective than infrastructure-wide development every time there’s a new patch.
Hardware & infrastructure challenges
With different devices, sensors and other hardware, often from different manufacturers, businesses need to adapt the software to help in connectivity, communication and the efficient streamlining of resources.
In this section, we will explore critical IoT challenges and solutions related to the hardware and physical risks of IoT devices. This includes:
- How to handle the additional data of new devices
- How to adapt to limited coverage
- How to conserve battery life for as long as possible
Scalability
A quick-scaling nature is both one of the biggest benefits and challenges of IoT development. More devices mean more data, and the ability for businesses to gain deeper insights and subsequent actions.
However, it also creates more data to process, more infrastructure to manage, and more connections to maintain. When making your first steps into the Internet of Things, you should prepare with scalability in mind. You may very well end up adding additional devices or technologies, after all.

Solution
When addressing scalability in IoT, it’s essential to tailor the solutions to the specific needs and context of your project. While some strategies may be universally beneficial, others should be carefully chosen based on factors such as the existing technological infrastructure, anticipated growth rate, or data volume.
- Modular architecture: This allows systems to expand through the addition of new modules without disrupting the existing infrastructure. Best for projects that anticipate gradual expansion and require a flexible approach to integration.
- Cloud computing: Cloud platforms inherently offer scalability, allowing systems to handle increased loads by adjusting resources dynamically. Ideal for projects with variable data loads and those that require remote access and collaboration.
- Edge computing: By processing data near the source, edge computing can reduce the amount of data that needs to be transmitted to the cloud, which is vital as the number of IoT devices grows. Suited for projects with real-time processing needs and those looking to minimize latency and bandwidth usage.
- Microservices: These allow for parts of a system to be scaled independently, which is much more flexible and scalable than monolithic system architectures. Effective for complex systems where different components may need to scale independently.
- Data management strategies: Effective data management is key to scalability as it ensures that the system is not overwhelmed by the volume of data generated by an increasing number of devices.
- Elastic load balancing: This is a network technique that ensures that the system can handle additional load by distributing traffic efficiently, essential for maintaining performance during scaling.
- Automated provisioning and deployment: Automation in deploying and integrating new devices can significantly streamline the scaling process. Recommended for projects with a high rate of device turnover or frequent updates.
- Quality of Service (QoS) protocols: These protocols help manage network resources by prioritizing certain types of traffic, which is crucial when the network is scaled up. Important for projects where certain types of data or operations must be prioritized to ensure performance.
- Standardized protocols: Using common protocols makes it easier to integrate and manage a growing number of devices from different manufacturers.
Selecting the right combination of these strategies is key to ensuring that your IoT system can scale smoothly and maintain performance over time. Remember, this list is not exhaustive or set in stone; it’s important to stay adaptable and consult with IoT specialists who can provide insights into the best practices and cutting-edge technologies tailored to your project’s specific scalability requirements.
Coverage & connectivity
Alongside consumption, we also need to consider every IoT sensor’s ability to transmit and receive data. In most cases, devices need to be connected at all times. A blip at the wrong time leads to unrecorded data, generating inaccuracies in your business solutions that rely on this respective data.
Let’s imagine a health app that tracks a user’s vitals. For the user, short range communication between their smartphone and corresponding health sensors on their body is generally not a problem. But what if we want to store data on a server somewhere? What if the users are in a location where WiFi is limited?
Naturally, this is the most critical for operations that are in remote locations. Not only do they suffer from lack of power options, they also have less access to the internet. As you might imagine, when it comes to Internet of Things risks, this is one of the biggest.
For example, where such coverage is a problem, one survey found that some of the biggest IoT challenges lay in reliability (47%) and security (42%). So it’s clear that ensuring consistent transmission is essential.
Solution
For businesses operating in remote areas where WiFi isn’t available, or where WiFi connectivity is limited, the tech industry offers several alternative connectivity solutions:
- Low Power Wide Area Networks (LPWANs): These networks use low-bandwidth data transmission with low bitrates, which is ideal for IoT devices that are not in close proximity to a network connection and need to conserve power while still being able to communicate effectively over long distances.
- Long Range Wide Area Networks (LoRaWANs): LoRaWAN is a specific protocol for LPWAN that uses Long Range (LoRa) radio frequencies, enabling communication over long distances. Devices using LoRaWAN are optimized for long battery life, with some capable of operating for up to 10 years on a single battery, depending on the application and transmission power.
- Bluetooth Low Energy (BLE): This is a power-efficient version of the traditional Bluetooth standard designed for short-range communication. While it’s well-known for its use in mobile phones, BLE has been adopted for a wide range of IoT applications. Unlike LPWAN technologies that can communicate over kilometers, BLE is typically suited for short-range communication up to 100 meters under optimal conditions. It allows for the exchange of data in short bursts, which reduces power consumption and extends the battery life of devices.
By understanding these connectivity options, businesses can select the most appropriate technology based on their specific needs, taking into account factors like range, power consumption, and data transmission requirements.
Example: IoT in Remote Agriculture
In remote farming areas, where establishing WiFi is impractical, IoT devices aid in precision agriculture. They can monitor crops and weather, relying on alternative connectivity:
- LPWANs: Connect widespread soil sensors to central systems, suitable for vast fields.
- LoRaWANs: Transmit data over long distances, ideal for extensive rural monitoring.
- BLE: Serves smaller areas like greenhouses for low-power data exchange.
The other solution is to consider asynchronous data communication. In this model, sensors don’t send data in real-time, but wait until coverage is efficient. This is ideal for devices that have time out in the field, but still have regular charges or other periods where connectivity is stronger.
Limited battery life
Sensors and other common IoT devices are small. They have to be. That also means they have small batteries and, consequently, need to conserve power as much as possible to operate efficiently. Losing power is a problem on many fronts. Not only does it mean the sensors aren’t contributing data, impacting the wider system, but there simply might not be anyone on site to turn the devices back on.
Mobile phones have the benefit of nightly recharges, but what about environmental monitoring sensors in remote locations, wildlife tracking devices, or health and fitness wearables? These also need to survive as long as possible on a single charge.
Solution
In the previous IoT challenge regarding connectivity, we talked about both Low Power Area Networks, and asynchronous data transmissions. These help devices send low-bit rate transmission and only when needed, respectively, to preserve power. Through smart design, devices can be optimized to use as little power as possible while still achieving their primary goals. But these are not the only ways to solve the challenge of limited battery life in IoT. See other key examples below.
Power-optimizing protocols
Using power-optimizing protocols such as LTE-M (Long Term Evolution Machine Type Communication) can help extend battery lifetimes. Complicated names aside, it has two key features that are of particular benefit to solving these types of IoT challenges:
- Power-Saving Mode (PSM): Decreases power consumption when devices are inactive.
- Discontinuous Reception (DRX): Saves energy by shutting down the radio when it’s not required for data transfer.
Together, these functionalities can extend battery life for years and years. It’s worth noting that such features, along with others in the same vein, rely on carefully monitoring the usage patterns of IoT devices and reducing power consumption during periods of inactivity.
Energy harvesting & passive devices
Devices can be equipped to draw power from environmental sources, such as:
- Solar energy (light)
- Thermal energy (heat)
- Kinetic energy (movement)
This method not only provides a sustainable energy source but also significantly extends the operational lifespan of IoT devices, especially in remote areas.
An interesting example of IoT devices that utilize environmental energy harvesting is the so-called “passive devices”. These do not depend on batteries or power lines. Instead, they capture energy from the environment – such as light, heat, kinetic motion, or radio frequencies – and convert it into electrical energy. This negates the need for frequent battery replacements or recharging.
IoT routers
Lastly, implementing IoT routers can centralize the more power-intensive tasks, such as security protocols, which can help to conserve energy on connected devices. However, it is vital to ensure that these routers do not become the weakest security link in the network’s chain.
Remote access
Devices still need to be updated from time to time, whether it’s for compatibility or security reasons. Ideally, these need to be done remotely. When there are hundreds, if not thousands, of sensors and devices around, your business can’t afford to send on-site teams everywhere.
It’s also important for users, who might not have the time for device management, but nonetheless expect a world-class service from your business.
Solution
A common option is to utilize cellular networks to provide updates even when WiFi internet access is unavailable. This can also be effective in situations where the existing WiFi is not effective, such as when it limits data transmissions or blocks large updates.
Another option is to also ensure as much work is done online as possible. In other words, utilizing the cloud, IoT routers and other devices that do the processing and heavy lifting instead. This way, the major updates can be deployed in the cloud. This software-light approach also helps conserve power, too, as an added bonus.
Ease of integration
One of the best things about the Internet of Things is that it’s not a monolith. Devices and channels can be added or adapted all the time. It’s very likely that, in the future, you will implement new technologies, and therefore need to integrate them.
So, what’s the most scalable approach to do this? New devices means new data access, as well as ensuring smooth communication across the existing IoT system.
Solution
We’ve covered this one before, but it never hurts to repeat a good thing! With both the cloud and a well-prepared API layer, it’s effortless to implement new devices or systems into the existing software. The API layer ensures that you only need to adapt the new channels to this integration port, rather than adapting the entire system.

By using the cloud and an API layer, you maintain a focus on security as well, since a well-prepared team can restrict API access to only what’s necessary, ensuring unwelcome guests are unable to penetrate the system.
Business challenges
Finally, we want to focus on IoT challenges and solutions related to internal business aspects, such as the skills and knowledge necessary to implement IoT applications successfully. After all, it’s commonly known that any transformation is as much an internal, organizational change as it is a physical, hardware-based one.
So how can your business become IoT-ready? Here, we want to offer some advice on overcoming the less well-known IoT risks, namely quality control and securing the necessary development skillsets.
Quality control
Every IoT device impacts overall quality. It’s not just about the app or dashboard. As such, IoT technology brings a greater need for quality control. Whether it’s implementing new technologies, or simply ensuring sensors continue to operate in areas of poor connectivity, there are a lot more angles to consider when embracing the Internet of Things.
Solution
Automated processes really are your friend. The IoT is vast. You can not feasible update everything manually. Since every device is connected, automated tools can be used to test security, data, general usability, and more.
Custom scripts can be prepared to test essential parameters, creating automatic reports and even monitoring solutions that can flag quality issues the moment they reach a certain level or severity. Updates, likewise, can also be rolled out in a similar fashion, ensuring quality remains high.
Our other piece of advice is to invest in testing. If each new piece of software or hardware is fully tested, you’ll prevent a lot of problems ahead of time. For example, we readily test our mobile devices on common devices, using real hardware, for the best results. Why shouldn’t the same approach be applied across the board?
Development costs
One of the most daunting IoT challenges often occurs at the very beginning. The IoT is vast, so surely your expenses will be too, right? As we said at the start, however, this is only a problem if you enter into IoT development unprepared and without a keen plan.
Solution
There’s no rush to implement every possible device. As with most digital business applications, it’s better to start with a core understanding of user needs, and then implement a functioning prototype and an MVP version of the application.
In fact, this approach is highly recommended. It enables you to gain user feedback as quickly as possible, so your next decisions are made on tangible, real results.
Flutter stands out as an exemplary framework. Drawing from our experience, this cross-platform technology can reduce app development costs by up to 40%. This efficiency is achieved through Flutter’s ability to use a single codebase for deploying across multiple platforms, such as iOS, Android, and web.
Moreover, Flutter accelerates the time-to-market of your app. This means that you can relatively quickly create a functioning basic version of the product to effectively attract investors for its further development.
Development skill set
The very diversity of today’s technology is one of the biggest Internet of Things risks. How will you develop everything? The average developer has a large number of skills, but that often doesn’t cover cloud optimization, multiple app developments, cybersecurity, and more! The more ambitious the IoT systems, the more skilled professionals you will need along the way.
Solution
Call us a little biased on this one, but it’s perfectly acceptable to utilize outside help. If you don’t have an internal team with the necessary competencies for IoT development, outsourcing is likely your best solution, at least in the initial stages.
If you’re aiming to test your product concept, swiftly obtain feedback, or attract investors for further app development, it is typically more efficient and quicker to engage an experienced IoT developer team than to face the extensive and costly efforts of onboarding an internal team. This entails not just hiring, but also integrating new members into the project, establishing their roles, and defining effective processes – all of which can be a significant workload.
As your product evolves, the strategy of assembling an internal team becomes more practical. It’s important to choose a development partner who can ensure a smooth project handover to your in-house team when the time comes. This should be one of the key points in your early conversations with potential partners.
What else should you consider when choosing your IoT app development partner? We recommend evaluating potential companies in three key areas:
- Proven expertise in IoT development. Ensure your potential new partner is proficient in creating IoT applications. Check their portfolio to determine their experience in developing similar products. Assess their case studies and previous projects for suitable complexity and scale in line with your needs.
- Client feedback on IoT projects. It’s also important to see what previous clients think. Platforms such as Clutch and Good Firms can help provide these insights into a potential partner’s work ethic, reliability, and their ability to meet deadlines.
- Security awareness and prioritization. In early discussions, take the opportunity to check their understanding of security in regards to IoT Development. Ask how they protect data privacy, network security, and communication between devices. If they can explain their use of encryption, authentication protocols, and routine security checks, it’s a good sign that they prioritize security highly – and rightly so.
Don’t be afraid to be meticulous here. By taking the time to evaluate all three factors, you can ensure your chosen development partner has not only the requisite expertise but also values security and client satisfaction in their IoT projects.
- You may also like: IoT Applications: 7 Real-World Examples Across Industries
Let’s sum up the key challenges of Internet of Things:
Our experience in IoT development
At Droids On Roids, we have a solid track record in creating connectivity apps that help our clients achieve their business goals and high ROI. With over 10 years of experience in IoT projects across 5 different industries, from healthcare to entertainment, our work speaks for itself – just check out our reviews on Clutch.
Get in touch – we’d love to discuss your project and prepare a tailored proposal for you.
IoT challenges: where should you start?
With so many possibilities, where should you start? It’s crucial not to be overwhelmed by the Internet of Things. Instead, concentrate on your users, their needs, and the problems your IoT solution aims to solve. Begin by constructing a basic version of your app and then develop a roadmap based on user input. Like any app, responding to feedback and implementing changes as necessary is vital to meet business objectives.
Here, you will find some more tips on how to build an IoT solution of your dreams.
All of the challenges we’ve listed here are scalable. Whether your app is large or small, these challenges will always remain. By implementing them at the start, and focusing on practicality and quality over a wide-ranging system, you’ll be able to take bigger and bigger steps into the IoT.
Seek a partner for your IoT app development with a strong track record and an understanding of the critical importance of security. The right partner will support you with their talent and processes to achieve your business goals and maximize ROI.





0 responses to "Today’s 11 IoT Challenges and Solutions That Work"